I believe that the "delta of woot-project" attack exploits the SSH1 vulnerabilities. The following links describe the SSH1 exploit:
- SecurityFocus.com: [CORE SDI ADVISORY] SSH1 CRC-32 compensation attack detector vulnerability
- ADVISORY REGARDING SSH PROTOCOL VERSION 1 CRC-32 COMPENSATION ATTACK DETECTOR VULNERABILITY
- SecuriTeam.com: SSH1 'CRC-32 compensation attack detector' vulnerability leads to remote code execution
The attacker uses a C scanning program sshs.c (author Jenkins@madsite.org) which checks a list of IP addresses for the pressence of SSH-1.5-1.2.27 or SSH-1.99-OpenSSH_2.2.0p1. The vulnerabilities in SSH1 are exploited to gain root access.
It then installs new binaries so the commands "ps" and "pstree" used to monitor processes are useless when trying to find the hacker installed processes. It also installs new network monitoring binaries to replace "netstat" and many of the other commands you might use to diagnose system problems caused by the exploit. The exploit starts a few background processes, the purpose of which I do not fully understand. The exploit also creates a user "woot". This entry must be deleted from the files /etc/passwd and /etc/shadow. The attack results in a serious compromise of your system so extensive that I can not readily determine it's full extent. Again I recommend a full reinstall of your system and hard drive re-format (with new sector sizes).
See the YoLinux Internet Server Security Tutorial - Installing OpenSSH (using protocol SSH2) and avoid this problem!
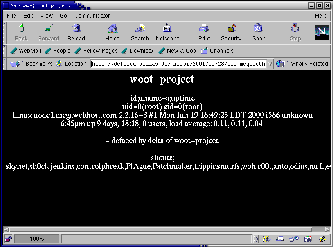
If the web page defacement was not a big enough clue that you have been hit with the "delta of woot-project" attack, you can also use the "chkrootkit" tool to audit your system and find many of the known trojans.
Download chkrootkit from http://www.chkrootkit.org/
Un-tar the package and compile:
- make sense (Compile C programs)
- ./chkrootkit (Run shell script and call programs.)
I am certain that this will NOT report all the trojans left on your system.
Hacker file discovery:
- Find regular non-device files hidden in /dev: find /dev -type f -print
The file /dev/MAKEDEV is acceptable.
Results: /dev/cui220 and /dev/cui221 (Config files used by hacker trojans.) - Find executables set with "stickey" bit so that they execute with root privileges (many of these are legit):
- find / \( -perm -4000 -o -perm -2000 \) -type f -exec ls -ldb {} \;
- find / -type f -perm +6000 -ls
- Find hidden cleverly named executables:
- find / -name "..." -print
Result: /home/httpd/cgi-bin/... CGI left by hackers for web access of comprimised server. - Clever dot and space for a file name: find / -name ". " -print
- find / -name "..." -print
Let me start by saying that one may not be able to fully recover the system. I recommend that you reinstall the operating system and re-format your hard drive with new sector sizes. The following was more of an experiment to see how clean I could get the system after this attack. I also wanted to try and discover how extensive and damaging the "delta of woot-project" exploit was and gain insight into the attack.
My first attempt to remove trojan binaries failed:
[root prompt]# rm /bin/ps
rm: remove write-protected file `/bin/ps'? y
rm: cannot unlink `/bin/ps': Operation not permitted
The trojaned binaries could not be deleted at first. One must change the file attributes first using the chattr -i file-name command.
chattr -i /bin/ps
rm -f /bin/ps
The following is a list of binaries I deleted and the Red Hat RPM used to replace them.
/bin/hostname
/sbin/ifconfig
/bin/netstat
/sbin/arp
/sbin/ipmaddr
/sbin/iptunnel
/sbin/plipconfig
/sbin/route
/sbin/slattach
rpm -ivh --force net-tools-...rpm
/bin/bash
rpm -ivh --force bash-...rpm
/sbin/klogd
/sbin/syslogd
rpm -ivh --force sysklogd-...rpm
/sbin/sysctl
/bin/ps
rpm -ivh --force procps-...rpm
/usr/lib/mgetty+sendfax
/sbin/vgetty
/sbin/mgetty
rpm -ivh --force mgetty-...rpm mgetty-viewfax-...rpm mgetty-voice-...rpm mgetty-sendfax-...rpm
/usr/lib/libgpm.so
rm -f /usr/lib/libgpm.so
/usr/lib/libgpm.a
rpm -ivh --force gpm-...rpm gpm-devel-...rpm
/usr/bin/pstree
/sbin/fuser
rpm -ivh --force psmisc-...rpm
/usr/sbin/in.rlogind
/usr/kerberos/bin/rlogin
rpm -ivh --force rsh-...rpm rsh-server-...rpm
/usr/lib/bind - Change directory attribute: chattr -i /usr/lib/bind
/usr/lib/nslookup.help
rpm -ivh --force bind-...rpm bind-devel-...rpm bind-utils-...rpm
/bin/basename
/bin/date
/bin/echo
/bin/false
/bin/nice
/bin/pwd
/bin/sleep
/bin/stty
/bin/su
/bin/true
/bin/uname
rpm -ivh --force sh-utils-...rpm
/sbin/depmod
/sbin/genksyms
/sbin/insmod
/sbin/insmod.static
/sbin/ksyms
/sbin/lsmod
/sbin/modinfo
/sbin/modprobe
/sbin/rmmod
/sbin/rmmod.static
/sbin/kerneld
rpm -ivh --force modutils-...rpm
/usr/lib/uucp
rpm -ivh --force uucp-...rpm
/bin/mount
/bin/umount
/sbin/swapon
rpm -ivh --force mount-...rpm
/sbin/mingetty
rpm -ivh --force mingetty-...rpm
/sbin/installkernel
/sbin/cardctl
/sbin/cardmgr
/sbin/ftl_check
/sbin/ftl_format
/sbin/ifport
/sbin/ifuser
/sbin/pcinitrd
/sbin/probe
/sbin/scsi_info
rpm -Uvh --force kernel-...rpm kernel-utils-...rpm kernel-ibcs-...rpm kernel-doc-...rpm kernel-headers-...rpm kernel-pcmcia-cs-...rpm
Also:
at-...rpm
uucp-...rpm
fileutils-...rpm
The "delta of woot-project" exploit also installed /sbin/ipchains-l and pt07 background processes and binaries.
It is important to use the command pstree -p or ps -auxw
to find rogue processes and kill them: kill -9 process-id
(The newly installed commands ps and pstree.
The hacker replaced the original commands with
versions which hide the hacker processes)
Also reset inetd/xinetd processes. View boot configurataion: chkconfig --list | grep on
Turn off any process you do not wish to run: chkconfig --del init-process
See init scripts in the directory /etc/rc.d/init.d/
To turn off anonymous FTP, edit /etc/ftpaccess:
Change class all real,guest,anonymous * to class all real,guest *
This got changed by the attacker.
The most obvious and important change is to the /etc/passwd and /etc/shadow files. Delete the entry "woot".
Update: The box was hacked again. Probably a trojan back door left behind after the first attack. A DOS (Denial Of Service) network load was generated by launching a process called slice2.
To further clean things up I updated the system with the latest kernel RPM. Lets see if these guys break in again. I'll keep you posted.
I discovered a very clever backdoor. The CGI program /home/httpd/cgi-bin/... was left behind. A very clever hiding of a backdoor I had not found the first time. Running the strings command against this executable reveals that it is a method of executing any command input by the user via the web. Of course it had the "Sticky" bit set to execute with the privilege of root. (Crafty buggers)
A DOS attack was launched from the host against its victims by the hacker. The misnamed process was called squid and it wouldn't die and was re-spawned each time. The top command was used to identify the process. I removed the line in the file: /etc/inittab
8:2345:respawn:/usr/sbin/squid
At this point, we had no more time to devote to this exercise so we gave up and put in the new drive with a new install.
Conclusion:
If your system has been comprimised by this or a similar attack, then it's time to realize that you can't win. Wipe the drive and re-install the OS.
- YoLinux Tutorial: Securing your internet Linux server - How to monitor and prevent hackers from gaining control of your system.
- OpenSSH.org
- Analysis of SSH CRC32 Compensation Attack
- Basic Steps in Forensic Analysis of Unix Systems - I highly recommend reading this article!
(more security articles by Dave Dittrich) - The Coroner's Toolkit (TCT) - Data recovery. Tools for gathering or analyzing forensic data on a Unix system.
- SafeMode.org: scripts
Hacker IRC: irc.madsite.org:6667 #woot-project
 |
"Hacking Linux Exposed"
by Brian Hatch, James B. Lee, George Kurtz ISBN #0072127732, McGraw-Hill From the same authors of "Hacking Exposed". |

|
 |
"Maximum Linux Security: A Hacker's Guide to Protecting Your Linux Server and Workstation"
by Anonymous and John Ray ISBN #0672321343, Sams Covers not only audit and protection methods but also investigates and explains the attacks and how they work. |

|
 |
"Network Intrusion Detection: An Analyst's Handbook"
by Stephen Northcutt, Donald McLachlan, Judy Novak ISBN #0735710082, New Riders Publishing |

|
 |
"SSH, the Secure Shell : The Definitive Guide"
by Daniel J. Barrett, Richard Silverman ISBN #0596000111, O'Reilly & Associates |

|
 |
"Computer Security Incident Handling Step by Step"
by Stephen Northcutt ISBN #0967299217 |

|
 |
Security Source Magazine
Security Source Magazine's cover story is about keeping the network secure, from the gateway to the desktop. Subscribe now and continue to learn about valuable security topics and strategies in each quarterly issue. |
Free Subscription |
 |
Info Security Magazine
Business and management of information security. It is an international magazine, with an European focus. It is published in both print and digital editions, the latter containing the full content of the print publication, accessible via the web. Its experienced editorial team delivers stories that deal with the big picture issues of information security. Our sources and columnists are the expert security researchers and practitioners who define, drive, and lead the field. And our journalists are in demand by the IT trade and broadsheet press. |
Free Subscription |


 Books:
Books: